DMARC is a nice mail security setup to protect against forged emails. But even better is how it can actually get participating hosts to send you emails about how your emails are being seen. And if anyone is forging, phishing, or otherwise misusing your domain.
Setup your DNS records
It uses DNS TXT record to specify your settings. Here’s an example one to start off with:
Name: _dmarc.example.com
Value: v=DMARC1\; p=none\; rua=mailto:[email protected]\;
We won’t go into too much detail, but the record uses _dmarc before the domain. The p=none means to only monitor the email traffic. We can change that to quarantine which will suggest to the remote mail server to put email that fails DKIM/SPF checks in the spam folder. Or reject which will instead tell it to reject the message if it fails DKIM and/or SPF tests.
Now, the rua is the cool one. This will suggest to the mail server that it sends the specified email a report to the given email about emails that it gets, and as to whether they passes or failed, and why.
Note
For the rua= you need to use an email on the same domain
Note
Some dns providers may not like the \;. Just use ; and you should be ok.
To help you create it, you can use the DMARC Creator and Inspector to help you make it, if you’d like. Once you have it, and have allowed the DNS to propagate, you can check it with various checkers. The previous link also has a checker.
Organize the reports
Once you setup the above DNS record, you are going to get some emails (usually only up to 1 per day per provider that has received emails from you). They will have a zip file of an xml file that contains the data about the email(s) it received from your domain.
It would be nice to have something to accept these and to parse the information.
One such program is dmarcts-report-parser. It will parse the email account where the emails come, and put them neatly into a database.
On the home page / Readme, it will show the needed packages to install. And you’ll need to have a MySQL server to store the data in. Then you can download or clone the directory:
git clone https://github.com/techsneeze/dmarcts-report-parser.git
The Readme also tells how to configure the dmarcts-report-parser.conf file, which is fairly straightforward. I opted to just have it use IMAP to get the emails, but you can also just tell it the folder where it’s located, the mbox, or even where the xml files are.
Viewer
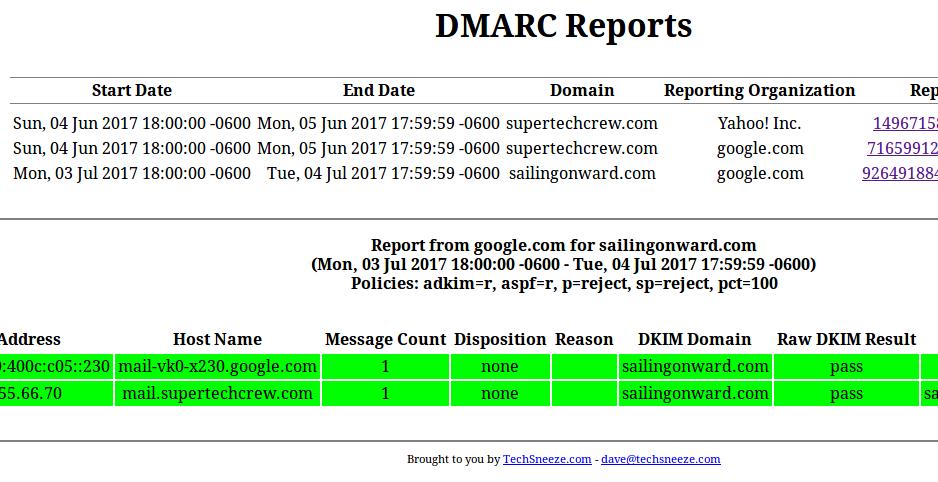
So now we have a lot of data in a database. That’s boring and hard to read. Here’s a viewer that can take those reports and show them in an easy to read way (with colors).
It needs a webserver like Nginx or Apache, PHP, and access to the mysql/mariadb database where the above script has saved it’s information.
Info
Remember to also install the mysql php module.
You can download the script into a folder that the webserver/PHP can access:
git clone https://github.com/techsneeze/dmarcts-report-viewer.git
Be sure to secure the script from outside users, via a htpasswd file or other such protection. Copy the config file, and change the values in it to match your database setup:
cp dmarcts-report-viewer-config.php.sample dmarcts-report-viewer-config.php
$dbhost="localhost";
$dbname="dmarc";
$dbuser="dmarc";
$dbpass="xxx";
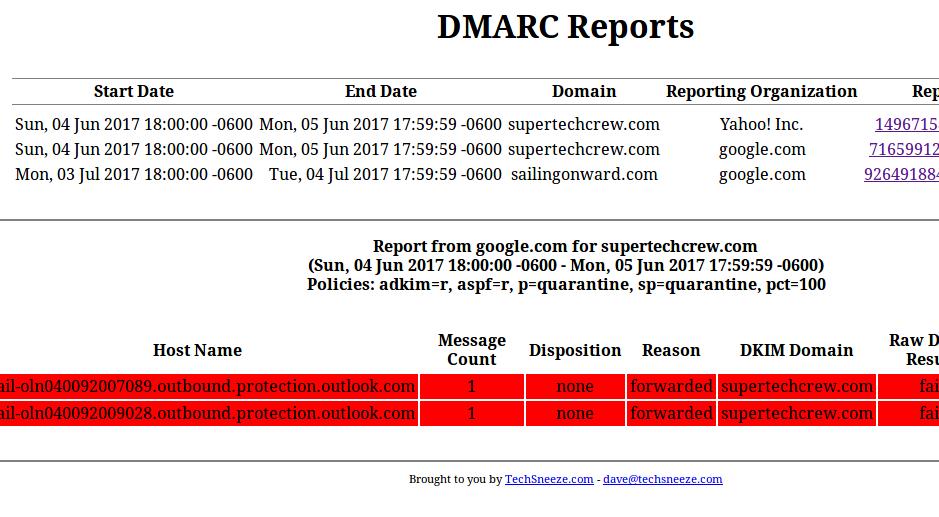
Once you set it up, it should look like the above picture, or this one (failures cause by forwarding emails):
Bonus
Want to get Forensic reports of the emails that are failing? Such as the emails that are failing, and who is sending them?
Attach fo=1\; to the DMARC record, specifying you want these Forensics reports. And then specify what email you want the reports to go to with [email protected]\;
So, adding these to the above DMARC record will give us:
v=DMARC1\; p=none\; rua=mailto:[email protected]\; [email protected]\; fo=1\;
Note
These emails can’t be used by the above script nor the viewer. They are the full emails so you can see what is being sent, and by who. It’s still really useful!