Wow. Wow. Wow.
Officially called CVE-2014-0160, the Heartbleed security exploit is such a simple yet far reaching bug.
And by now you’ve probably heard lots about it:
- Arguably the worst bug the internet has ever seen since the 90s.
- Previous traffic can be intercepted.
- Any data from a server may have been compromised.
- Server keys can be obtained.
- Requires users to reset their passwords.
- It’s been in the “wild” for over two years.
- That’s the really bad thing: how long it’s been out. All that traffic. NSA has probably been having a hay day.
But that’s no news. They always do.
Still, that is the way of software. And the way of human error. Unknown, unpredictable, and … real.
So what happened?
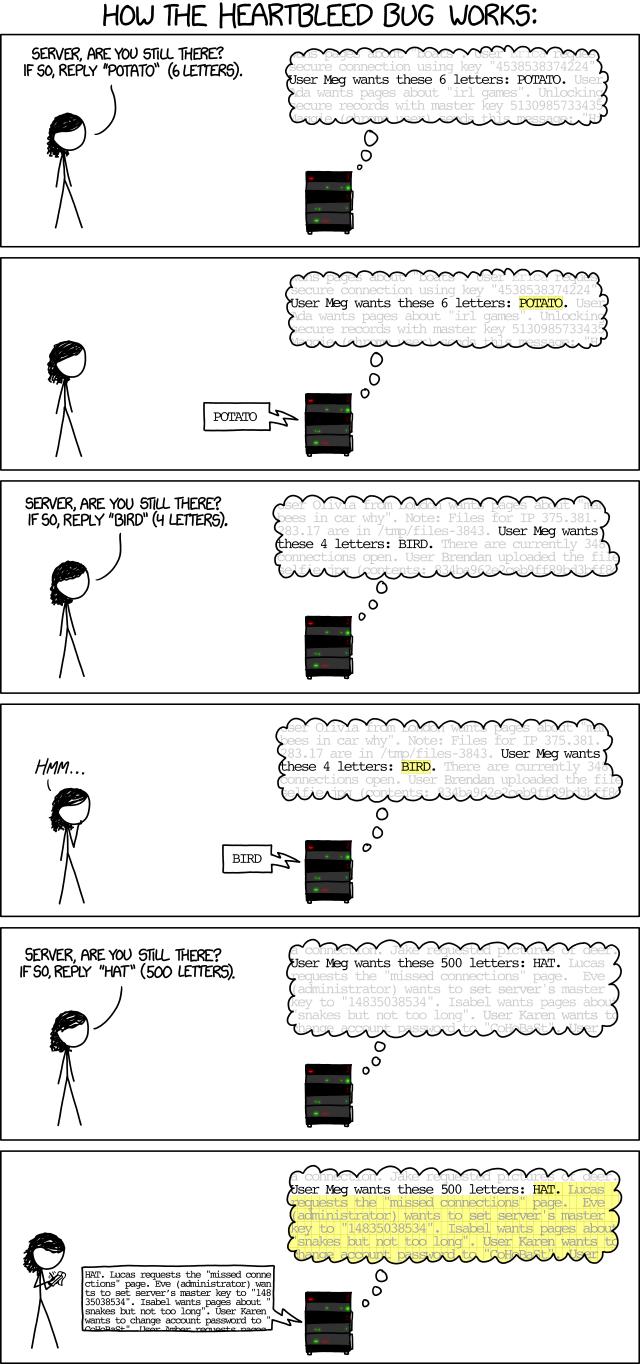
It has to deal with the Heartbeat extension of OpenSSL. Let’s take a look at a very Scientific Explanation:
So, in other words:
- The client sends a bit of data to keep the connection open.
- Only problem is OpenSSL doesn’t check the length of the data sent.
- A user “says” they sent a 500 length string
- But actually they send a 4 letter word
- Server gives the user back 496 characters of server memory, which can include keys, documents, passwords, credit cards, etc.
- User gets the main encryption key, and can decipher all past, present, and future traffic… instantly.
- That is, until the server admins change the server key, which some already have.
So, ya, it’s bad. As far as changing passwords, if the site was vulnerable, check that the site is not vulnerable anymore, and then change them.